2/ We learn that NSO Group had at least three @whatsapp exploits: Heaven, Eden & Erised.
The first, called Heaven, was active some time prior to Sept-Dec 2018. It worked by using manipulated messages to direct targeted devices to a malicious WhatsApp relay controlled by NSO Group.
Heaven was ultimately disabled by changes made in Sept & December 2018 by WhatsApp.
storage.courtlistener.com
The first, called Heaven, was active some time prior to Sept-Dec 2018. It worked by using manipulated messages to direct targeted devices to a malicious WhatsApp relay controlled by NSO Group.
Heaven was ultimately disabled by changes made in Sept & December 2018 by WhatsApp.
storage.courtlistener.com
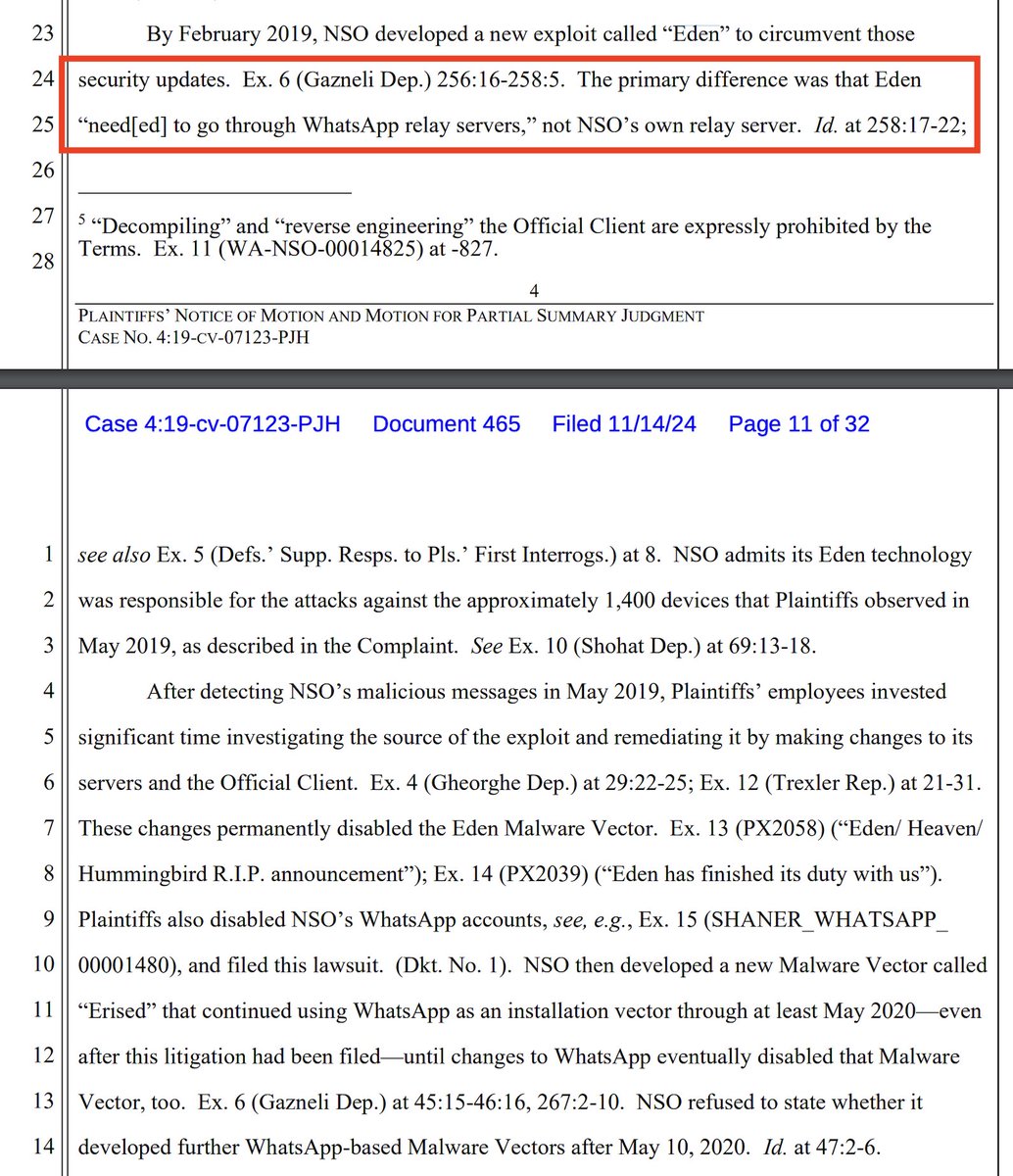
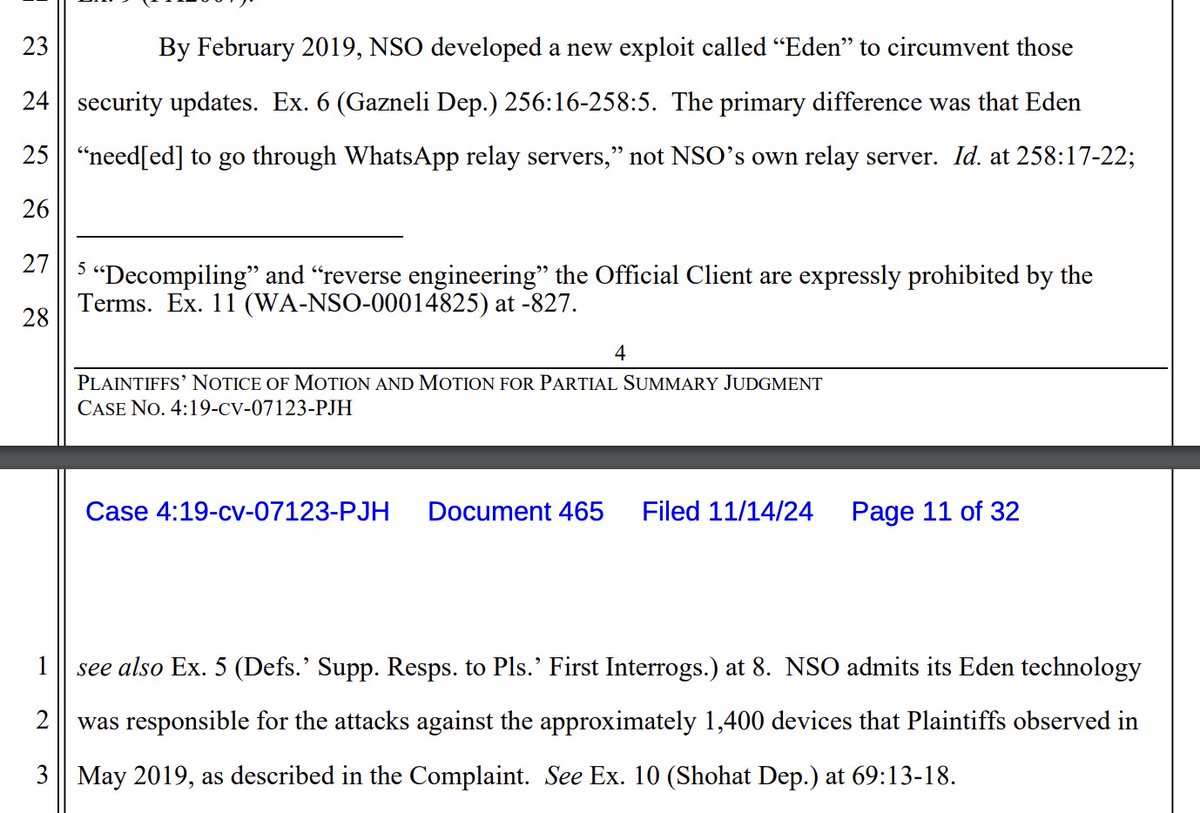
3/ After the Heaven vector stopped working, NSO Group deployed Eden, which had a key feature: it needed to pass through relays controlled by @WhatsApp.
There's some detail about how the exploit was deployed to avoid detection.
Ultimately, it was detected, leading to the lawsuit.
There's some detail about how the exploit was deployed to avoid detection.
Ultimately, it was detected, leading to the lawsuit.
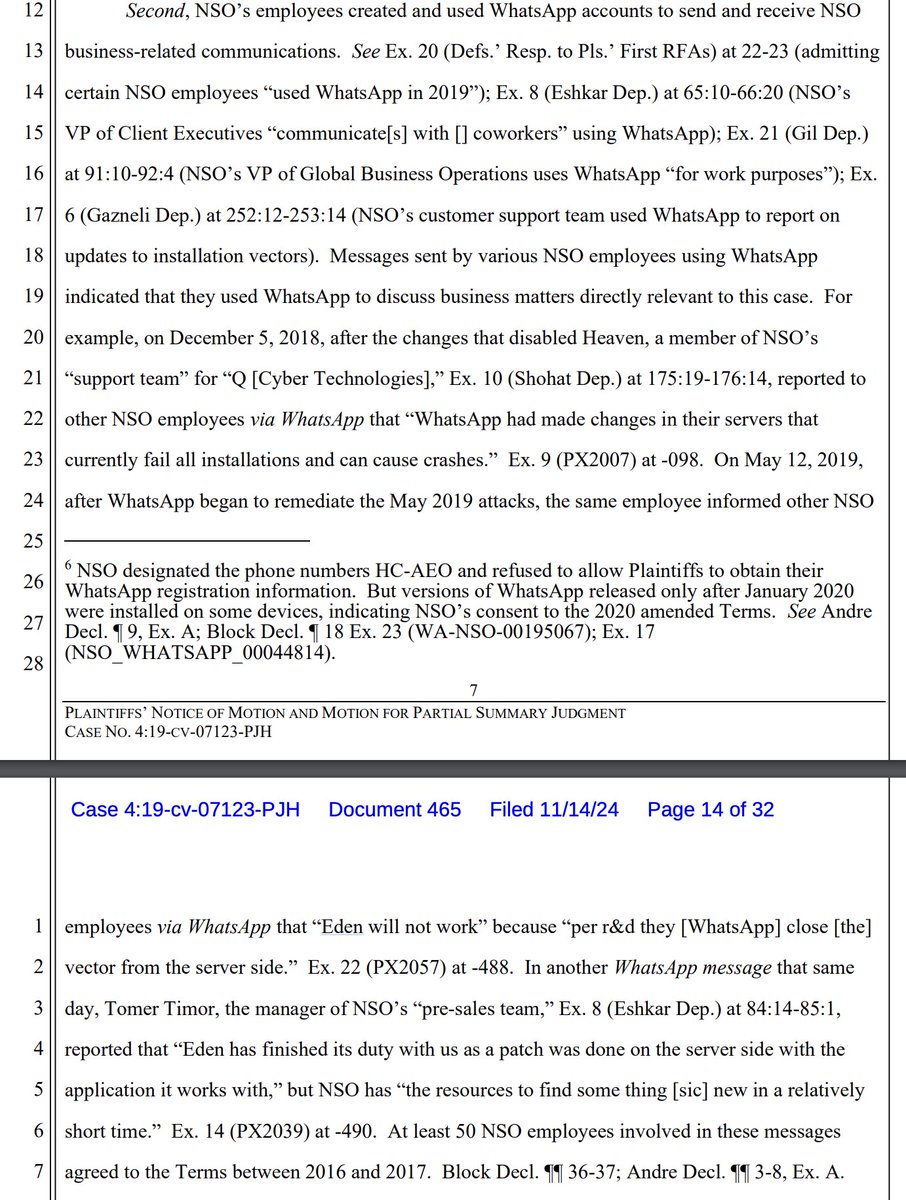
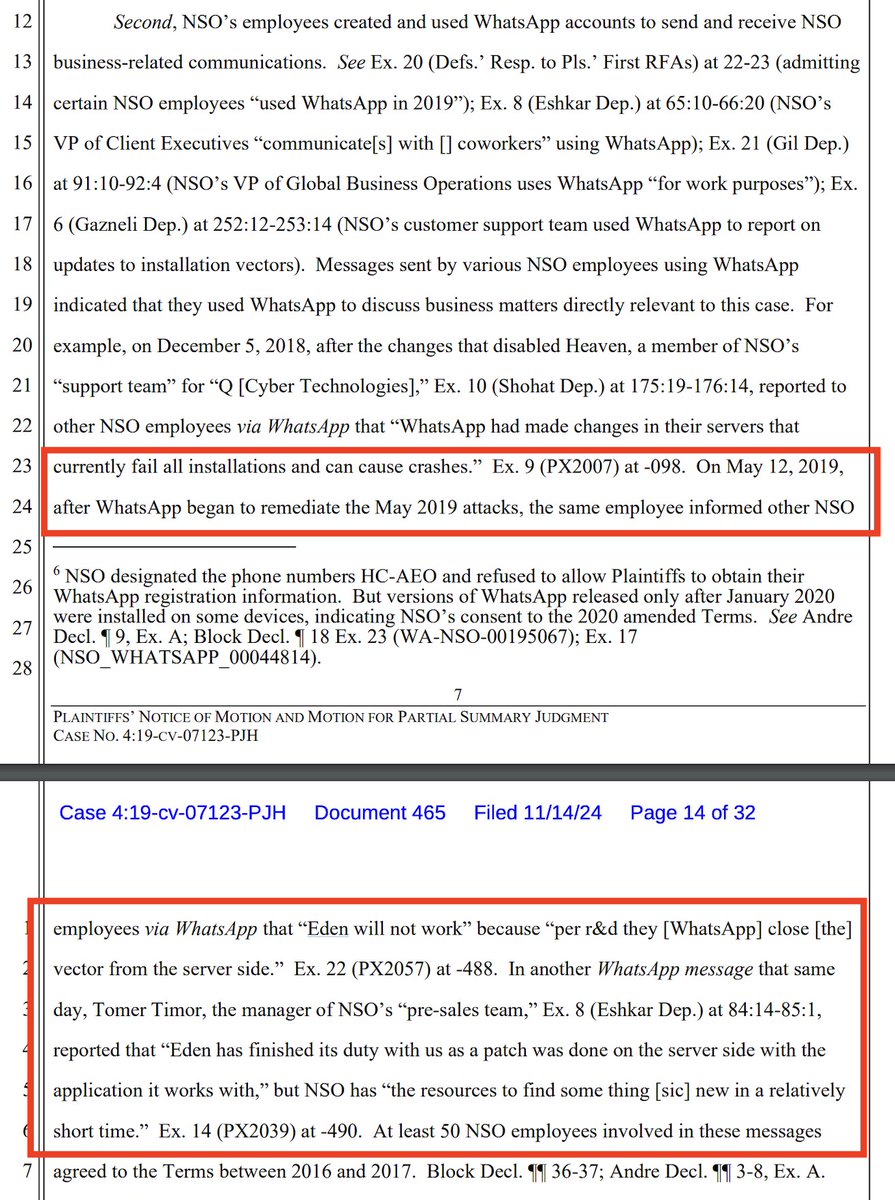
4/ In a series of WhatsApp messages apparently produced in discovery... we have NSO Group employees discussing the end of Eden... as @WhatsApp's mitigations took hold in 2019...
...And a mention of what was apparently to come, the third exploit Erised, which was allegedly active until sometime after May 2020.
storage.courtlistener.com
...And a mention of what was apparently to come, the third exploit Erised, which was allegedly active until sometime after May 2020.
storage.courtlistener.com
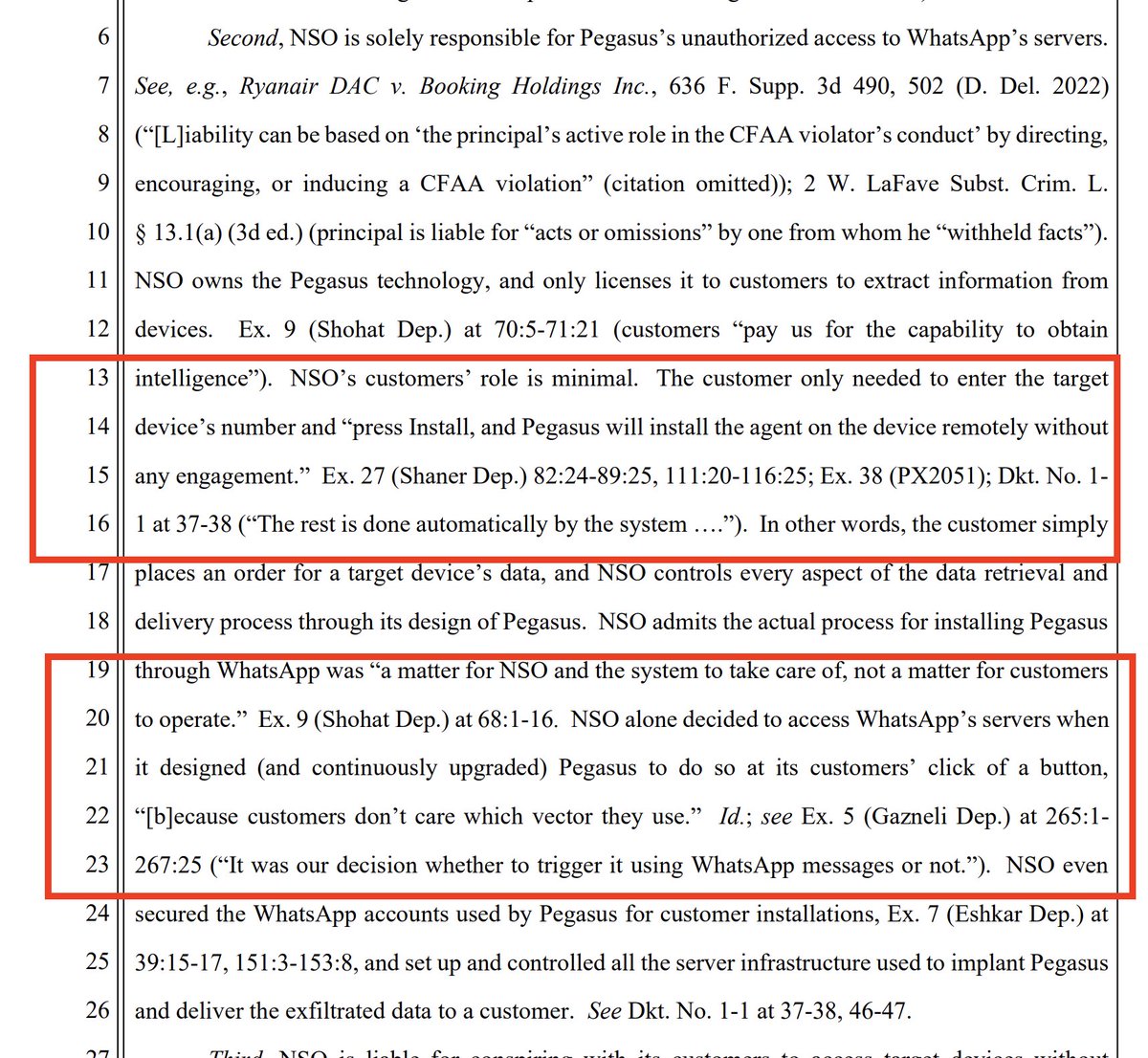
@WhatsApp 5/ Super interesting: discussion by @WhatsApp suggesting just how much of the work of hacking was allegedly done by NSO Group's systems.
Not the spyware customers.
While this matches what many of us have believed, seeing it laid out like this is new.
storage.courtlistener.com x.com
Not the spyware customers.
While this matches what many of us have believed, seeing it laid out like this is new.
storage.courtlistener.com x.com
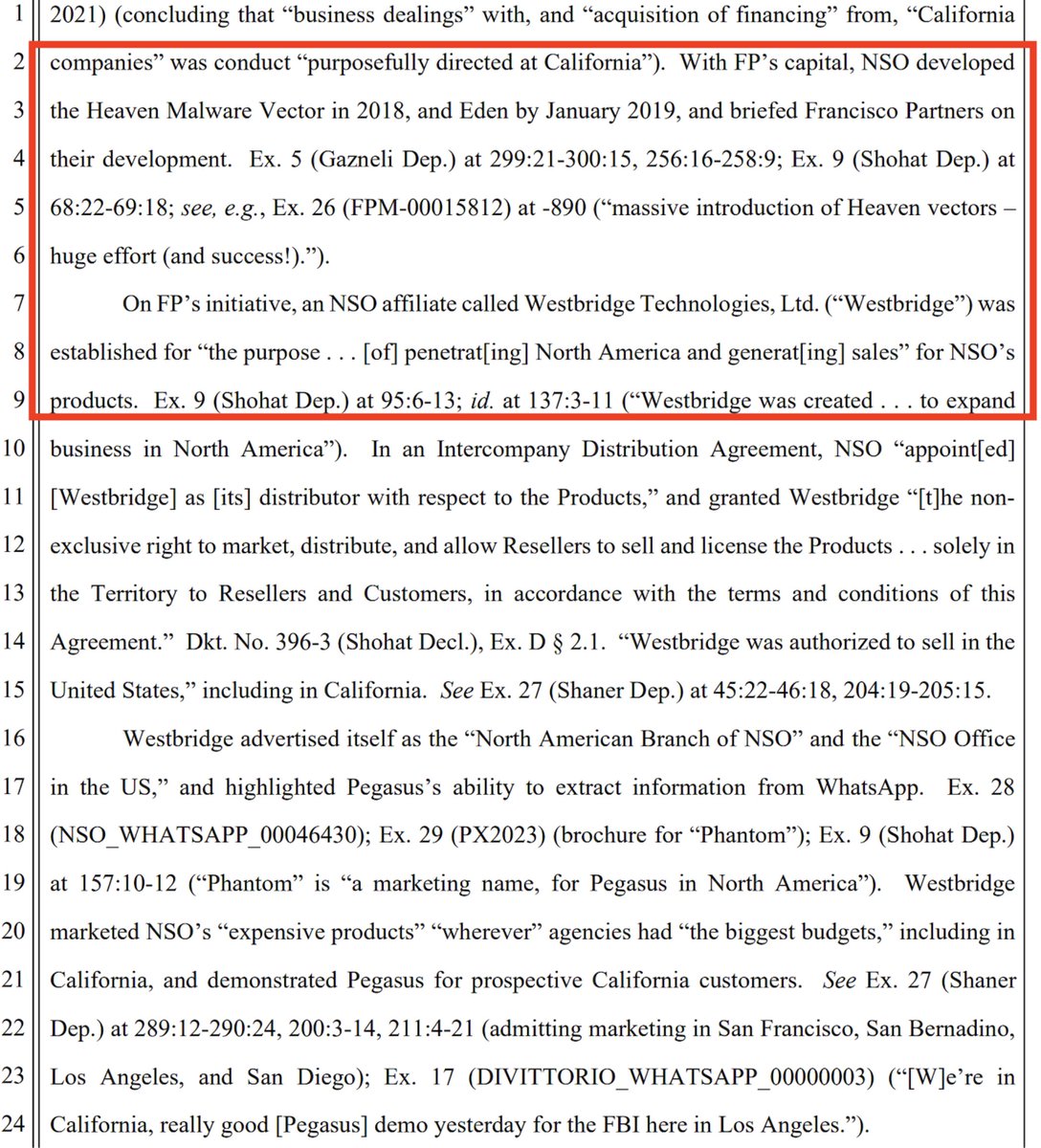
6/ NSO Group's US-based owners at the time, Francisco Partners, are characterized by @WhatsApp as getting briefed on the rollout of the Heaven exploit.
That's interesting.
As is the private equity firm's alleged initiative in moving NSO to sell Pegasus to US customers...
storage.courtlistener.com
That's interesting.
As is the private equity firm's alleged initiative in moving NSO to sell Pegasus to US customers...
storage.courtlistener.com
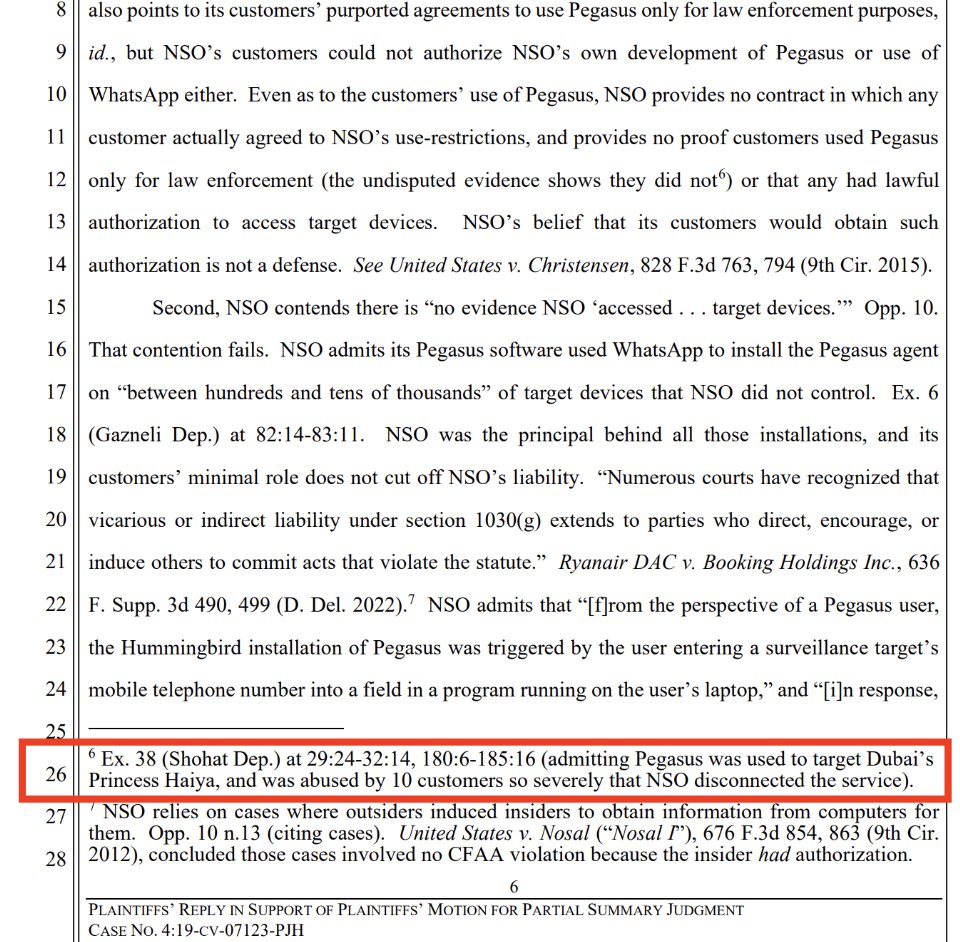
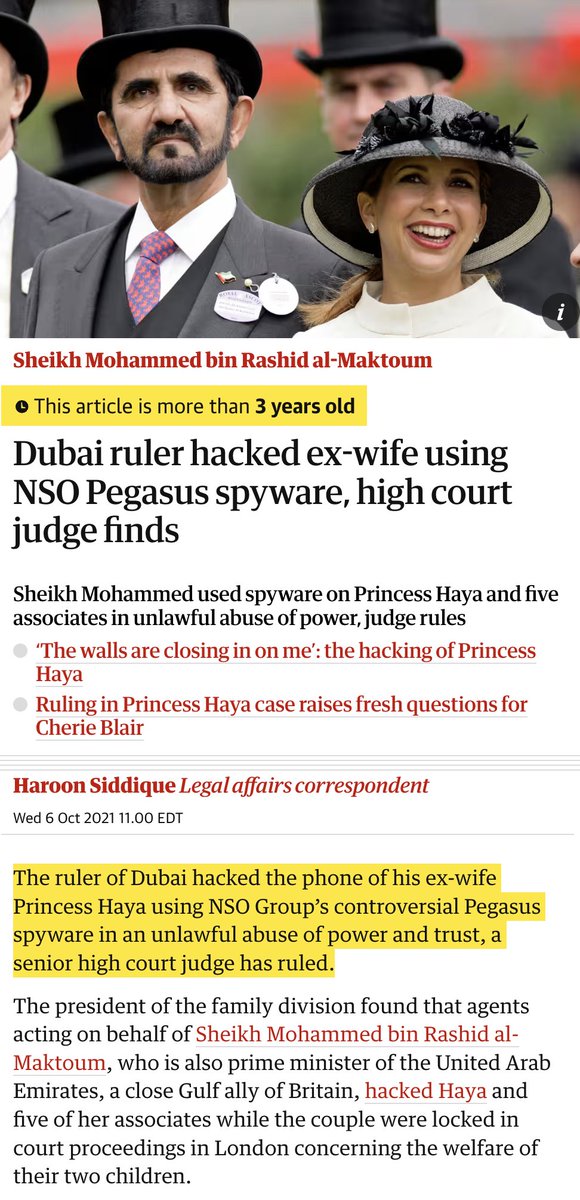
7/ And here's the promised footnote stating that NSO Group's CEO admitted in a deposition that #Pegasus spyware was used to target Dubai's Princess Haya.
Apparently confirming a finding made by a UK high court judge 3 years ago that Dubai's Ruler hacked the princess, his ex-wife.
@WhatsApp filing: storage.courtlistener.com
Article by @Haroon_Siddique theguardian.com
Apparently confirming a finding made by a UK high court judge 3 years ago that Dubai's Ruler hacked the princess, his ex-wife.
@WhatsApp filing: storage.courtlistener.com
Article by @Haroon_Siddique theguardian.com
جاري تحميل الاقتراحات...