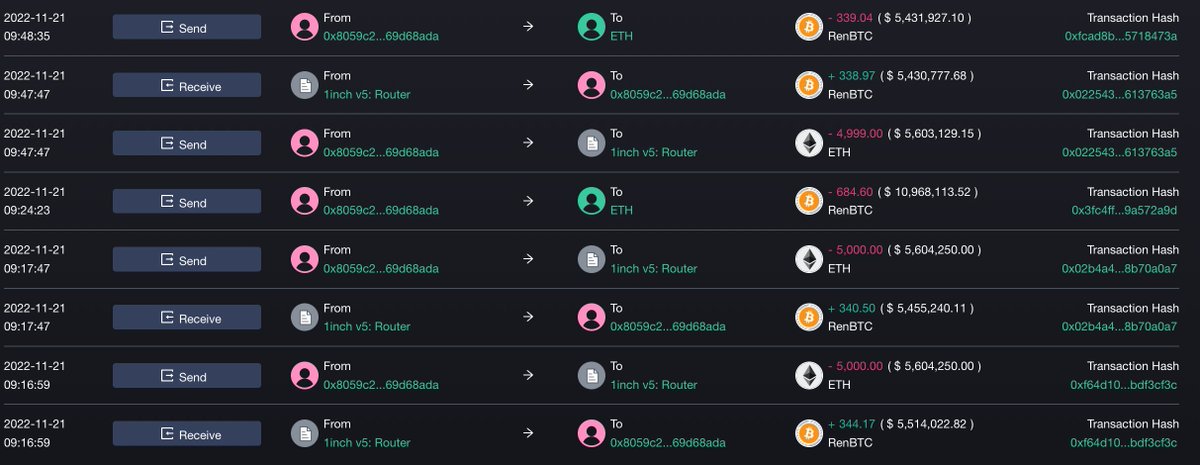
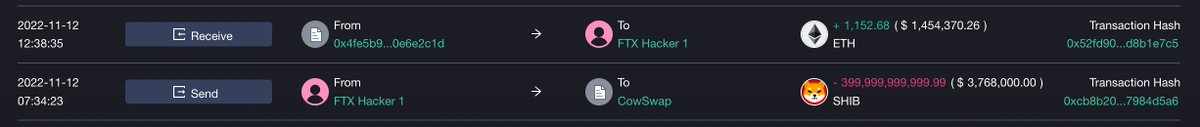
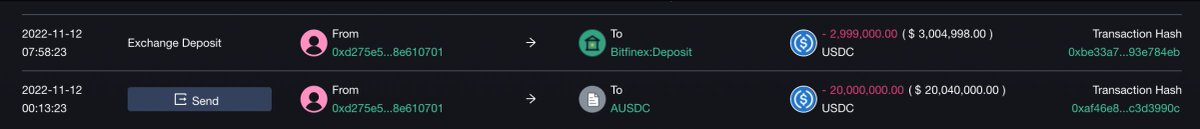
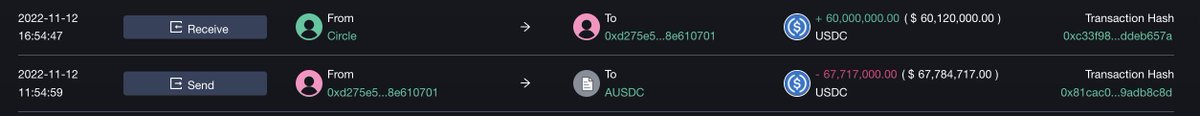
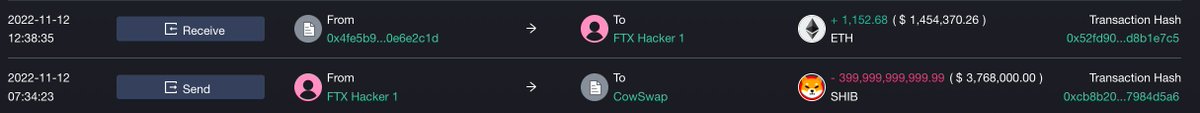
We find a smart money (or dark money?) address that always borrows >$10M USDC/ETH and deposits it to exchange every time before FTX-drainer dumps ETH.
Chances are he knows the activity of FTX-drainer and benefits from it:
🧵
Chances are he knows the activity of FTX-drainer and benefits from it:
🧵
⌛️2022-11-21
8:00 0xd275 began to transfer $USDC to the exchange. #Binance
9:16 Hacker began to sell $ETH to get $RenBTC.
8:00 0xd275 began to transfer $USDC to the exchange. #Binance
9:16 Hacker began to sell $ETH to get $RenBTC.
جاري تحميل الاقتراحات...