للمهتمين في مجال #الأمن_السيبراني #أمن_المعلومات
سأذكر تحت هذه التغريدة عدة نقاط من تشابتر 1
لشهادة (+CSA / محلل الأمن السيبراني) التي تتطلب خبرة 3-4 سنوات.
Chapter 1
Defending Against Cybersecurity Threats
سأذكر تحت هذه التغريدة عدة نقاط من تشابتر 1
لشهادة (+CSA / محلل الأمن السيبراني) التي تتطلب خبرة 3-4 سنوات.
Chapter 1
Defending Against Cybersecurity Threats
1-Cybersecurity analysts are responsible for protecting the confidentiality, integrity, and availability of information and information systems used by their organizations.
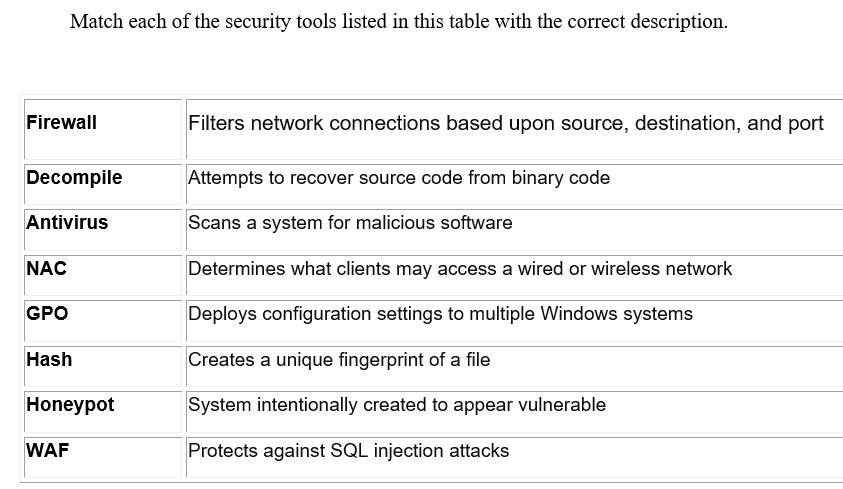
2-. Cybersecurity professionals develop and implement security controls, including firewalls, access control lists, and encryption, to prevent unauthorized access to information.
3-Availability controls, such as fault tolerance, clustering, and backups, seek to ensure that legitimate users may gain access as needed.
5-A threat in the world of cybersecurity is an outside force that may exploit a vulnerability. For example, a hacker who would like to conduct a DoS attack against a website and knows about an Apache vulnerability poses a clear cybersecurity threat.
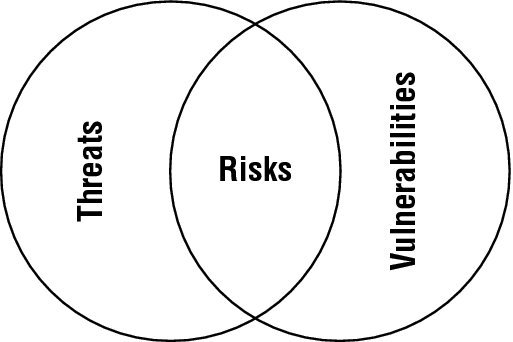
6-A risk is the combination of a threat and a corresponding vulnerability. Both of these factors must be present before a situation poses a risk to the security of an organization.
7-The relationship between risks, threats, and vulnerabilities is an important one, and it is often represented by this equation:
Risk = Threat × Vulnerability
Risk = Threat × Vulnerability
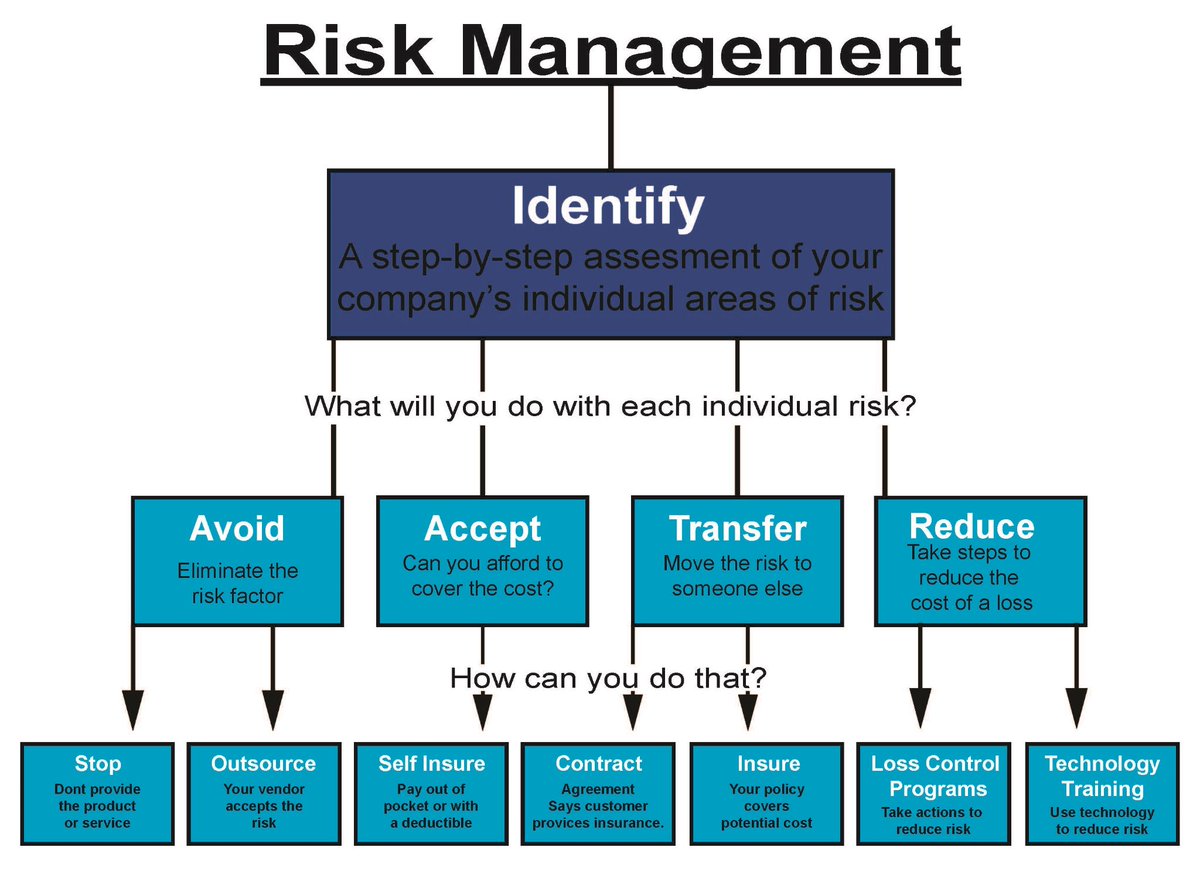
10-Technical controls are systems, devices, software, and settings that work to enforce confidentiality, integrity, and/or availability requirements. Examples of technical controls include building a secure network and implementing endpoint security.
11-Operational controls are practices and procedures that bolster cybersecurity. Examples of operational controls include conducting penetration testing and using reverse engineering to analyze acquired software.
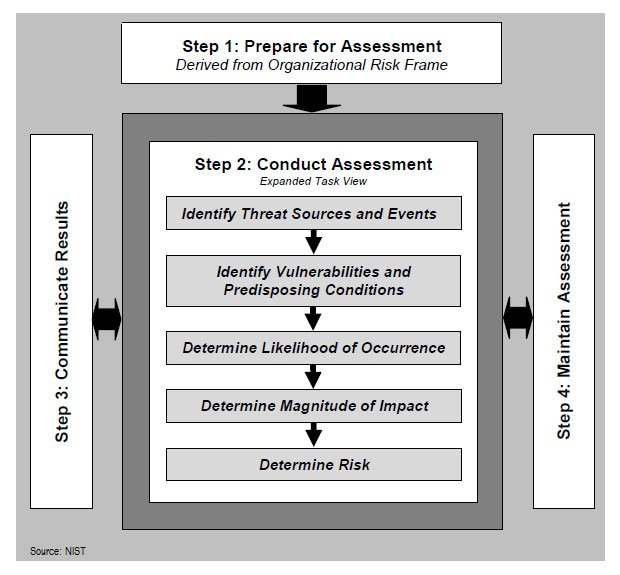
13-The NIST SP 800-30 risk assessment process suggests that an organization should identify threats and vulnerabilities and then use that information to determine the level of risk posed by the combination of those threats and vulnerabilities.
youtube.com
youtube.com
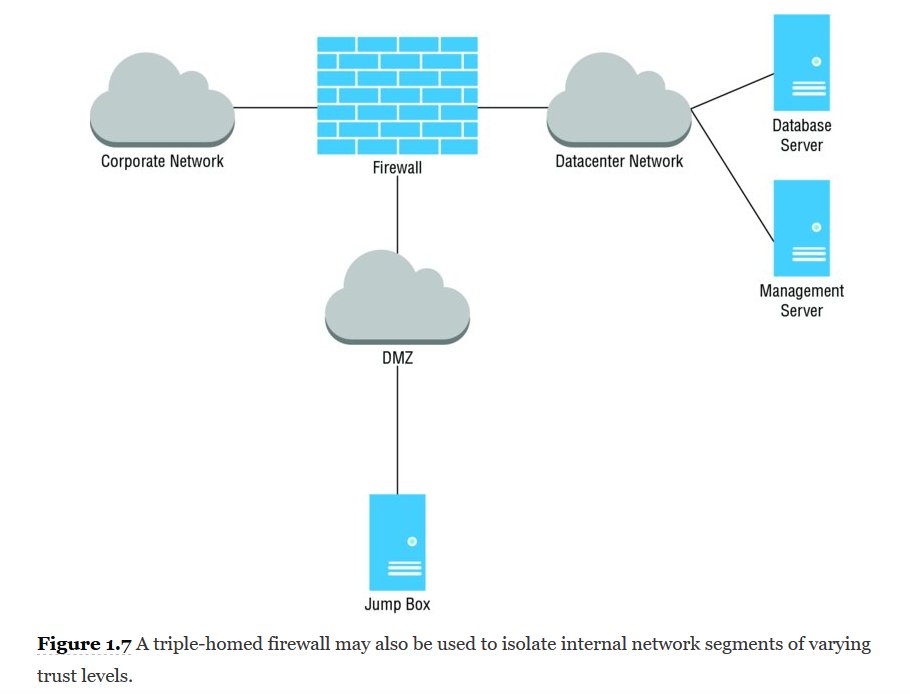
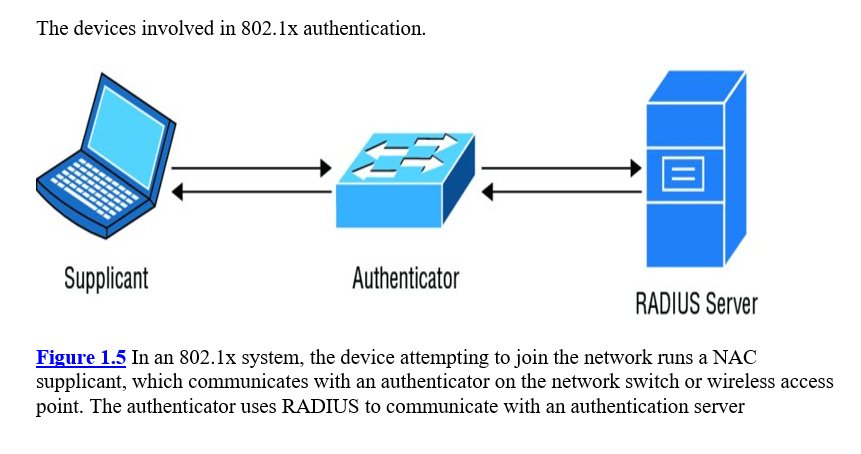
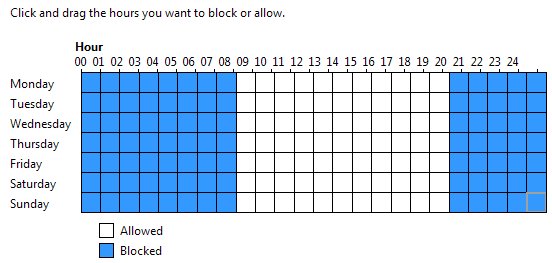
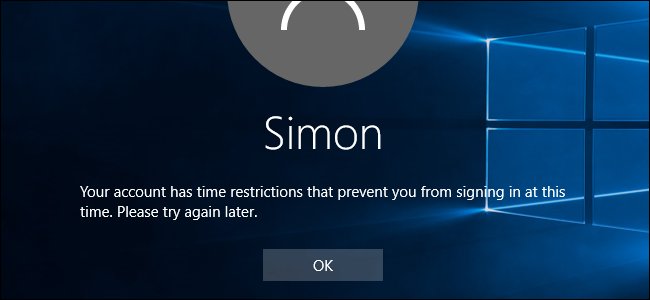
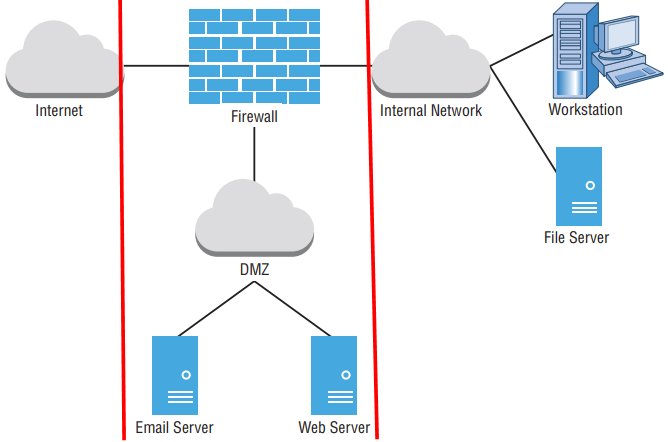
17-The “captive portal” NAC solutions found in hotels that hijack all web requests until the guest enters a room number are examples of in-band NAC.
19-Out-of-band NAC solutions, such as 802.1x, leverage the existing network infrastructure and has network devices communicate with authentication servers and then reconfigure the network to grant or deny network access, as needed.
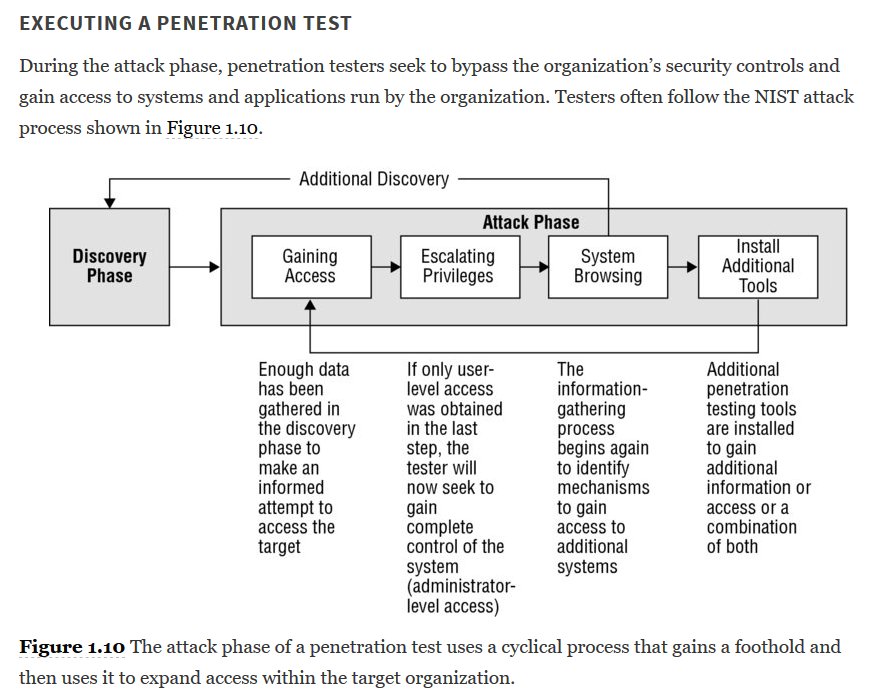
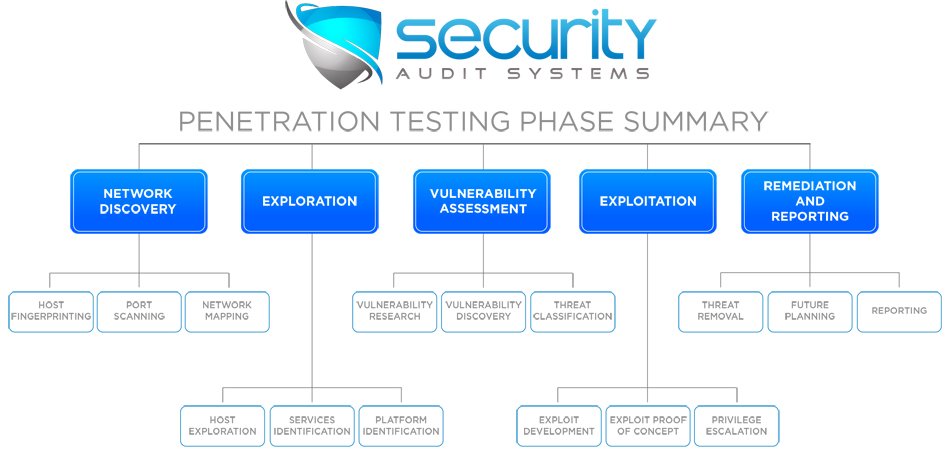
24-The attack phase of a penetration test is also known as the exploitation phase. Questions on the exam referring to test execution, the attack phase, and the exploitation phase are all referring to the same thing.
26- A threat in the world of cybersecurity is an outside force that may exploit a vulnerability.
27-The red team plays the role of the attacker and uses reconnaissance and exploitation tools to attempt to gain access to the protected network.
27-The red team plays the role of the attacker and uses reconnaissance and exploitation tools to attempt to gain access to the protected network.
28-The blue team is responsible for securing the targeted environment and keeping the red team out by building, maintaining, and monitoring a comprehensive set of security controls.
جاري تحميل الاقتراحات...